Can-CWIC CTF 2017 rev me easy writeup
hi there
in this article i'll tell you how i solved the rev me easy
challenge in can-cwic ctf 2017,so let's go
first the challenge look like the image below
after downloading the file
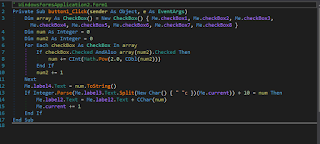
Let’s take a look at the binary in IDA
so as we saw it is pretty simple
it is just move group of values one by one to edx then xor it with the value in eax
now what is the value in eax
let's scroll up a little bit and we found it it is 0x10
so after i collect all the values that been mov to edx and xored
in order to solve the challenge i wrote a python script that do
the same operation the app do and print the result wish supposed to
be the flag
cc = "" bb = [] aa = [0x56,0x5c,0x51,0x57,0x6b,0x42,0x23,0x66,0x75,0x62,0x63,0x79,0x7e,0x77,0x4f, 0x79,0x25,0x4f,0x7e,0x20,0x64,0x4f,0x64,0x78,0x71,0x64,0x4f,0x78,0x71,0x62,0x74,0x2f,0x6d,0x7] for a in aa: bb.append(a^0x10)
for b in bb: cc += (chr(b)) print(cc)
first it xor every value in aa with 0x10 the it append the it to bbwish become the xored values list second it will convert every value in bb from hex to char and storeit into ccthen finally it will print cc and here is our flag




تعليقات
إرسال تعليق