Oman National Cyber Security CTF Quals \ GUI I
The challenge:
Category: Malware Reverse Engineering
Level: easy
Points: 50
The correct input is the flag,format flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}
Challenge Link: https://s3-eu-west-1.amazonaws.com/hubchallenges/Reverse/GUI.exe
The solution :
I open the GUI.exe using dnspy tool because it is a .net file
it contains form with 8 check boxes and button and 4 labels
when you hit the button the label will change to number
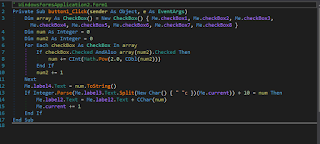
when i take a look at the button click event i saw this
the code is very simple
every time the button clicked it takes the number 2 raised to the power num2
num2 is the index of the checkbox that we checked it from array
then calculate the result and store it in num
so we Jumped into conclusion :
checkbox1.checked = array(0) >> num = math.pow(2,0) = 1
checkbox2.checked = array(1) >> num = math.pow(2,1) = 2
checkbox3.checked = array(2) >> num = math.pow(2,2) = 4
checkbox4.checked = array(3) >> num = math.pow(2,3) = 8
checkbox5.checked = array(4) >> num = math.pow(2,4) = 16
checkbox6.checked = array(5) >> num = math.pow(2,5) = 32
checkbox7.checked = array(6) >> num = math.pow(2,6) = 64
checkbox8.checked = array(7) >> num = math.pow(2,7) = 128
checkbox2.checked = array(1) >> num = math.pow(2,1) = 2
checkbox3.checked = array(2) >> num = math.pow(2,2) = 4
checkbox4.checked = array(3) >> num = math.pow(2,3) = 8
checkbox5.checked = array(4) >> num = math.pow(2,4) = 16
checkbox6.checked = array(5) >> num = math.pow(2,5) = 32
checkbox7.checked = array(6) >> num = math.pow(2,6) = 64
checkbox8.checked = array(7) >> num = math.pow(2,7) = 128
after that it checks if num is equal to number from the label3 + 10
if we go to InitializeComponent
we found that label3.text is
then lablel2.text = char of num
it sound clear that label3.text value is the flag
we can code simple python script to get our flag by taking every number in label3
and add 10 to it or we can try to get the correct pattern of check boxes for
every letter from the flag
the first way by using this python script :
num = "92 98 87 93 113 95 105 85 106 94 95 105 85 89 87 91 105 87 104 85 89 95 102 94 91 104 53 115" numb = num.split(' ') result = "" for a in numb: result += chr(int(a)+10) print(result)


تعليقات
إرسال تعليق