Hook-me write up

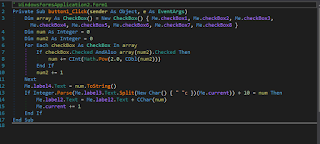
Syria National CTF (Finals) Hook-me challenge we had an android app named hook-me, back to the time of the competition we solved the challenge by de-compiling the apk and patching the smali code then recompile the app and signing it to get the flag , since that time i felt there should be another way to solve it using hooking so i decide to write this write-up after finding the second way to solve this hook-me . by de-compiling the apk and viewing its source code using apktool and dex2jar or simply using Jadx if you have no idea what i'm talking about then i recommend you read this guide Android App Reverse Engineering 101 then back to continue reading this post. when you view the source code you will see the following : as you see we have to change DoSomeMagic(55); to DoSomeMagic(256); then the flag will be displayed so to do this without patching the apk we can use a great tool called Frida but i never used it before so i have to read the documentation https://frida.re/docs/andr...